Your Margins Will Thank You
Deliver continuous compliance tailored to your cybersecurity services with the only platform purpose-built for MSSPs.






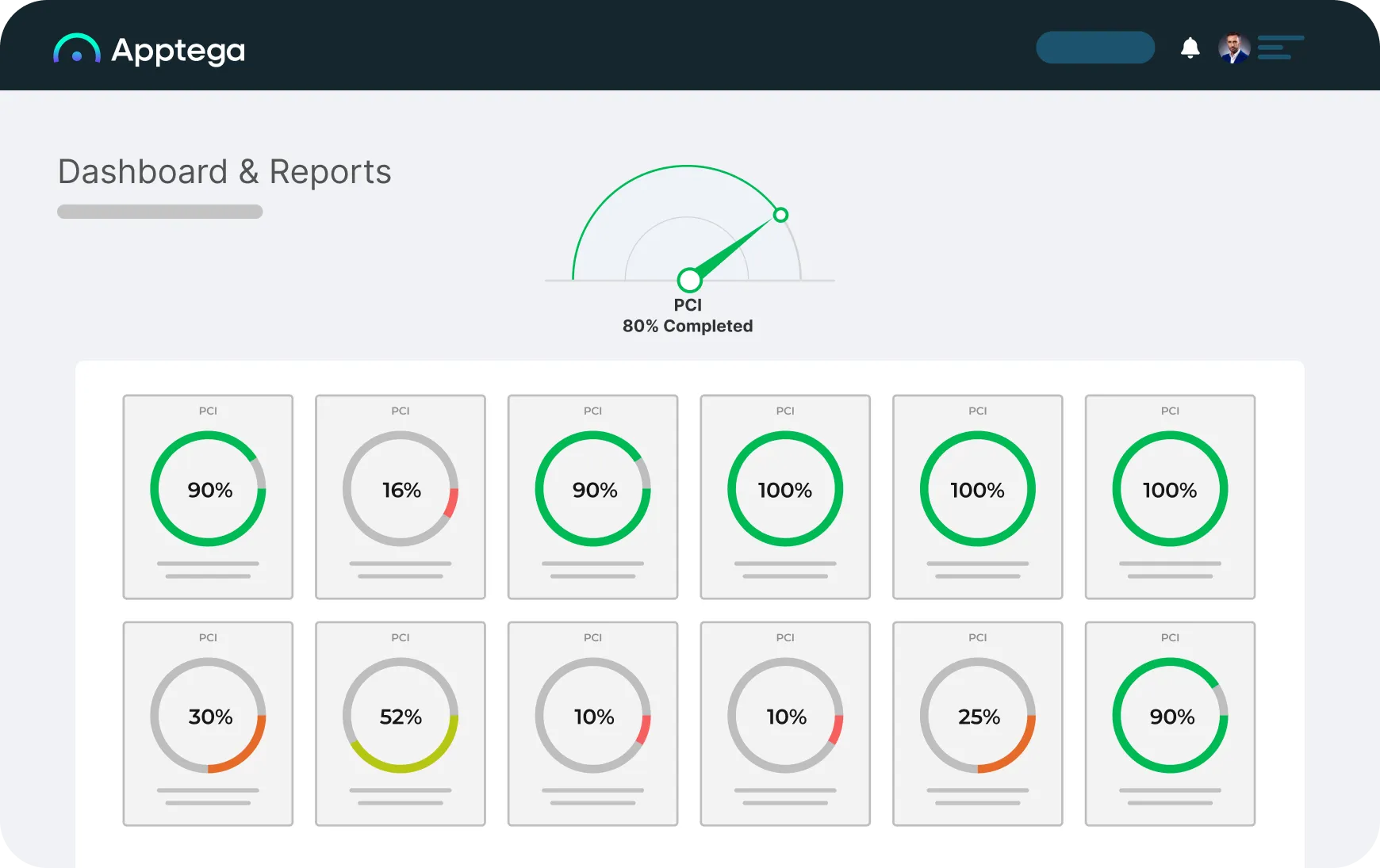
Create & manage all your compliance programs as one
With End-to-End Automation, from assessments to Risk Management to Audits
Automate
Automate assessments against 30+ frameworks
Speed through intuitive, questionnaire-style assessments that update your compliance score and identify risks as you go.
AI-driven recommendations at the sub-control level show you where you’re gapped and build the remediation playbook.

Build & Manage
FAST TrACK audit-ready programs that scale
From gap analysis to out-of-the-box risk management, vendor risk management and audit prep, cut the time it takes to manage and build world-class compliance programs in half.

Harmonize
Say goodbye to repetition with intelligent crosswalking MAPPED to 30+ frameworks
Need to comply with multiple frameworks? Don't even think about starting from scratch. Jumpstart your work by automatically mapping similar controls, then manage multiple frameworks as one simultaneous program.


Control & Report
Get an "Eye of Sauron" view with true multi-tenancy and persona-specific reporting
Manage separate programs, accounts, or clients from one god-level cockpit that gives you full, real-time visibility into how each is performing — and the customized reports to match.

ROI Stats that Speak Volumes
Calculate the actual value that world-class compliance programs can bring to your clients or your organization.
The cybersecurity revenue platform for MSSPs and channel partners
Want to grow your margins? Gain a competitive edge? Turn one-off projects into continuous compliance-as-a-service offerings? Do it all with Apptega, the go-to platform for channel providers dead-set on building big businesses.

.svg)
.svg)

.svg)
Connect directly to your sources of truth
Integrate with all your data systems and project management tools to streamline workflows and continuously monitor security status.
Apptega supports among the largest networks of integrations and an open API.

Impact stories
Hundreds of global partners and in-house security teams rely on Apptega to build world-class cybersecurity compliance programs. Here's how they do it.
Direct from the experts
Check out the latest news, resources and commentary from the Apptega team and a roster of veteran security and compliance professionals.


Ready to get started?
See Apptega action with a curated product demo. Or request a no-risk 14-day free trial.